You are likely aware that many of the smart devices in your home or workplace run on Linux. If you’ve ever wondered what distribution they run, the answer is probably none. They probably use a custom-compiled Linux kernel that minimizes its footprint and maximizes its security profile. This is typically accomplished via the Yocto Project.
The Yocto Project is an open source initiative that facilitates the creation of custom Linux distributions tailored for embedded systems and IoT devices. Rather than being a Linux distribution itself, it provides a framework and tools that allow developers to create their own distributions, optimized for specific hardware configurations or applications.
At the heart of the Yocto Project is the Poky build system, which uses the BitBake tool, a task executor and scheduler that is used to manage and create custom Linux distributions. It provides a layer-based architecture, which means that various components, such as the kernel, user-space applications, and metadata, are kept separate, making it easier to modify and manage individual aspects of the distribution.
Developers can use Yocto to create a lightweight, streamlined Linux distribution with only the necessary components for their specific use case, thereby reducing the footprint and improving the performance of the resulting system. This customization makes it a preferred choice for embedded systems where resources are limited and optimization is key.
AWS is a Platinum member of the Yocto Project. This means you know the meta-aws layer (available directly in Yocto’s repository) is extensively tested, stable, and supported with any new Yocto Project releases.
Fleet Provisioning
The AWS IoT Greengrass Core v2 agent can be installed into Linux and registered by hand into a specific AWS account every time:
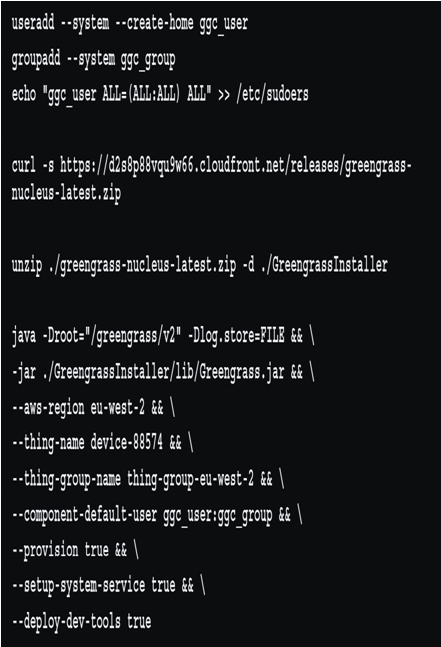
Figure 9.13 – Manual installation of the Greengrass v2 agent into Linux
The preceding code shows the procedure for manual installation. Keep in mind that before you run this, you must install the AWS CLI and configure it with credentials that have permission to perform all the steps needed to create the necessary objects in the target AWS account. For a large fleet of devices, this is labor-intensive and arguably insecure.
The Fleet Provisioning feature is an alternative approach that generates a set of claim certificates that are the same for all devices in a fleet – at first, anyway. Once the device boots for the first time, it reaches out to the AWS IoT Greengrass endpoints it has been configured for and exchanges its claim certificate for an individual certificate that uniquely identifies that device. From there, it operates in the same way as a manually provisioned device would. This is particularly useful for embedded Linux builds that use Yocto, which is why it is included in the meta-aws layer.
The following code shows an example of the configuration needed to install the Greengrass v2 agent and set up Fleet Provisioning for the local.conf file when doing a Yocto build that includes the meta-aws layer:
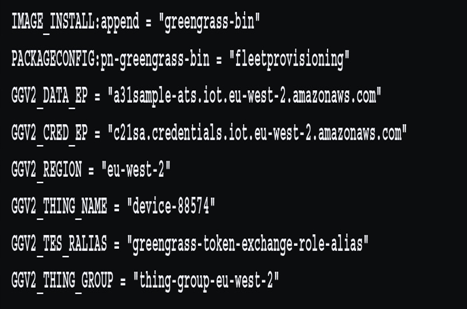
Figure 9.14 – Example of Fleet Provisioning configuration in local.conf for bitbake/Yocto