It is important that applications that span multiple geographies take into consideration the possibility that the closest AWS Wavelength Zone might change as a client device moves. A car with a 5G modem in it doing vehicle-to-everything (V2X) could easily drive from Boston to Philadelphia via New York – necessitating a switch between those three zones as it moves. Regardless of the discovery mechanism in use – be it triangulation, carrier-developed EDS, or self-developed EDS – the application should periodically re-evaluate the best carrier IP to use.
Extending a VPC into AWS Wavelength
When extending a VPC from a parent region into AWS Wavelength Zones, many of the considerations seen with AWS Outposts and AWS Local Zones remain the same.
Communication between AWS Wavelength Zones
Just as with AWS Outposts and AWS Local Zones, it is not possible to route traffic from one zone to another via the parent region within the same VPC. As shown in the next diagram, multiple VPCs must be configured, and a mechanism such as AWS Transit Gateway should be used to route between them within the parent region:
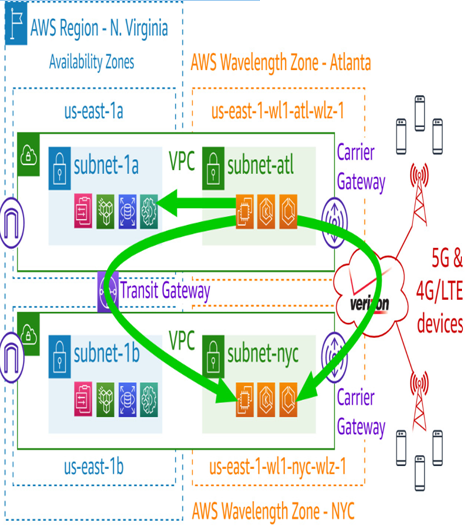
Figure 7.15 – Communication paths to other VPC subnets
It is, however, possible for resources in one zone to talk to resources in another over the MNO’s network using their carrier IPs.
Maximum Transmission Unit (MTU) values for AWS Wavelength:
9,001 bytes between EC2 instances within the same AWS Wavelength Zone
1,500 bytes across the carrier gateway
1,468 bytes between an AWS Direct Connect instance and an AWS Wavelength Zone
1,300 bytes between an EC2 instance in an AWS Wavelength Zone and an EC2 instance in a standard region
Communicating to AWS endpoints
In an AWS Region, you don’t need to think very hard when communicating with AWS services. The communication with them will happen via your internet gateway or network address translation (NAT) gateway as applicable. However, on a public subnet in an AWS Wavelength Zone, your route table will have 0.0.0.0/0 pointing to the carrier gateway:
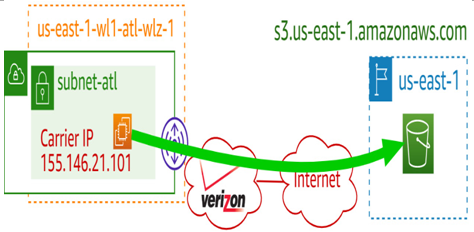
Figure 7.16 – Communicating with public endpoints over an MNO’s network
This means, by default, any connections open to AWS services such as Amazon S3 will traverse the MNO’s network to get to the internet – only to turn around and come back over the public internet to the parent region where the public endpoint lives:
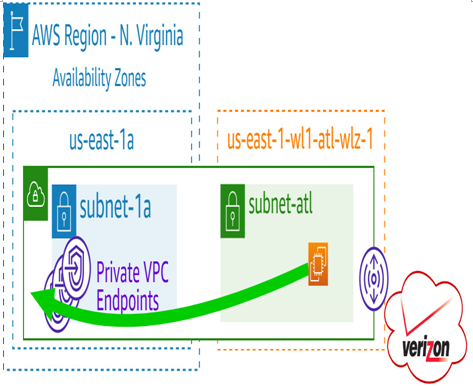
Figure 7.17 – Using AWS PrivateLink endpoints in the parent region
It is, therefore, recommended to use private endpoints for any AWS services your application needs to communicate with.